There’s nothing worse when preparing for a live event than anxiously waiting on the IT department of the host venue to find holes in the firewall to accommodate real-time video.
No matter what the venue – hotels, corporate offices, conference centers, or universities – they all have groups and systems designed to protect internal IT systems. So, if you don’t seek collaboration between broadcast engineers and the IT department in advance, you will put your video streaming capability seriously at risk. Read on to learn more about firewall traversal and how you can avoid potential live video streaming failures and frustrations.
Understanding Firewall Dynamics
Let’s start by explaining the basics of firewall dynamics. A firewall is the first line of defense in network security that keeps an organization’s information secure and away from prying eyes. The firewall’s job is to guard a LAN’s periphery with a WAN or the internet and prevent unauthorized connections and malicious software from accessing internal IT systems. It monitors incoming and outgoing traffic and, based upon defined security rules, decides what to block or allow. Without it, anyone could readily gain access to an organization’s internal networks.
The basic firewall task is simple. It knows that any exchange involves the bi-directional transmission of information between systems, from basic web surfing and file transfer to calling, conferencing, and video streaming. The firewall effectively does not allow for any communication to happen unless it’s initiated from within.
Firewall Traversal Explained
Firewall traversal is essentially a process used to implement a set of security policies that allow communication between different networks, without compromising security. At a basic level, unless otherwise provisioned, all systems behind the firewall must initiate communications (let’s call them a “caller”). When a “caller” reaches out to a “listener” (a system that’s outside the firewall across the internet) a bi-directional transmission (“communication”) is allowed.
The Firewall Challenge
When streaming real-time video, without the assistance of an intermediary system, many transport protocols such as RTMP make getting across firewalls a bit of a headache. They have rigid definitions of callers and listeners with video destinations typically behaving as “callers,” pulling the video from the source.
A cloud-based streaming server trying to pull video out of an event facility will likely be blocked by most firewalls. To enable video streaming, you’ll need to start negotiations with the IT department. The “caller” needs to be specifically included as a trusted external party (IP address) and the communication path between the specific internal IP address and the external IP address (port number) needs to be opened within the firewall.
The internal IP address must often be pre-established before programming the firewall – with another difficult task being the discovery and accommodation of IP address mapping within a facility. With all of this in mind, collaboration with the IT department is required, well in advance of your event.
SRT: Firewall Traversal Made Easy
When Haivision originally developed the SRT (Secure Reliable Transport) protocol, it was specifically designed for packet loss recovery and security, and also to assist in firewall traversal. In fact, it’s a feature that was championed internally by Haivision sales engineers who were regularly faced with firewall challenges.
SRT ensures easy firewall traversal by using a caller/listener handshake concept. The handshaking process used by SRT respects existing security policies by allowing outbound connections without requiring, permanent exterior ports to be opened in a firewall. The SRT protocol allows you to set endpoints to caller, listener, or rendezvous mode. Caller and listener modes are described above, with callers behind unknown firewalls to establish bi-directional data flows without the need for an IT administrator to open a port.
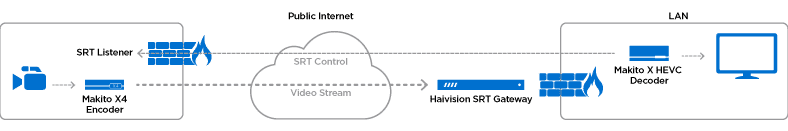
Even if there is no rule to explicitly allow an SRT destination device to communicate with the outside world, its control packets will nonetheless be able to return to the SRT source device (through the created firewall “hole”) because of the “connection tracking” feature of stateful firewalls. Rendezvous mode is particularly unique as it can create paths between two unknown firewalls or be used in the cloud (with Haivision SRT Gateway) as a central transfer node for SRT traffic.
Stream Multiplexing
SRT has recently augmented its firewall traversal techniques by supporting multiple streams with a single UDP port, otherwise known as multiplexing. This simplifies the challenges of firewall traversal for complex streaming workflows and is particularly useful in broadcast applications such as the remote production (REMI) of multiple live feeds.

Haivision SRT Gateway now features Stream ID, which allows users to send multiple SRT streams from different sources through a single UDP port and read the Stream IDs to decide how to route them from there. A major benefit to this is that it facilitates firewall traversal by only opening up one port and has only one listening socket on a server, rather than having to open a UDP socket for each stream that’s coming in. An IT department can dedicate a single port that can be used for any number of simultaneous SRT streams, preventing the need for broadcast engineers and video producers to request additional ports depending on the event covered.
You can learn more about how Haivision SRT Gateway and how it makes light work of firewall traversal here. DOWNLOAD THE DATASHEET

